StealthMem Architecture
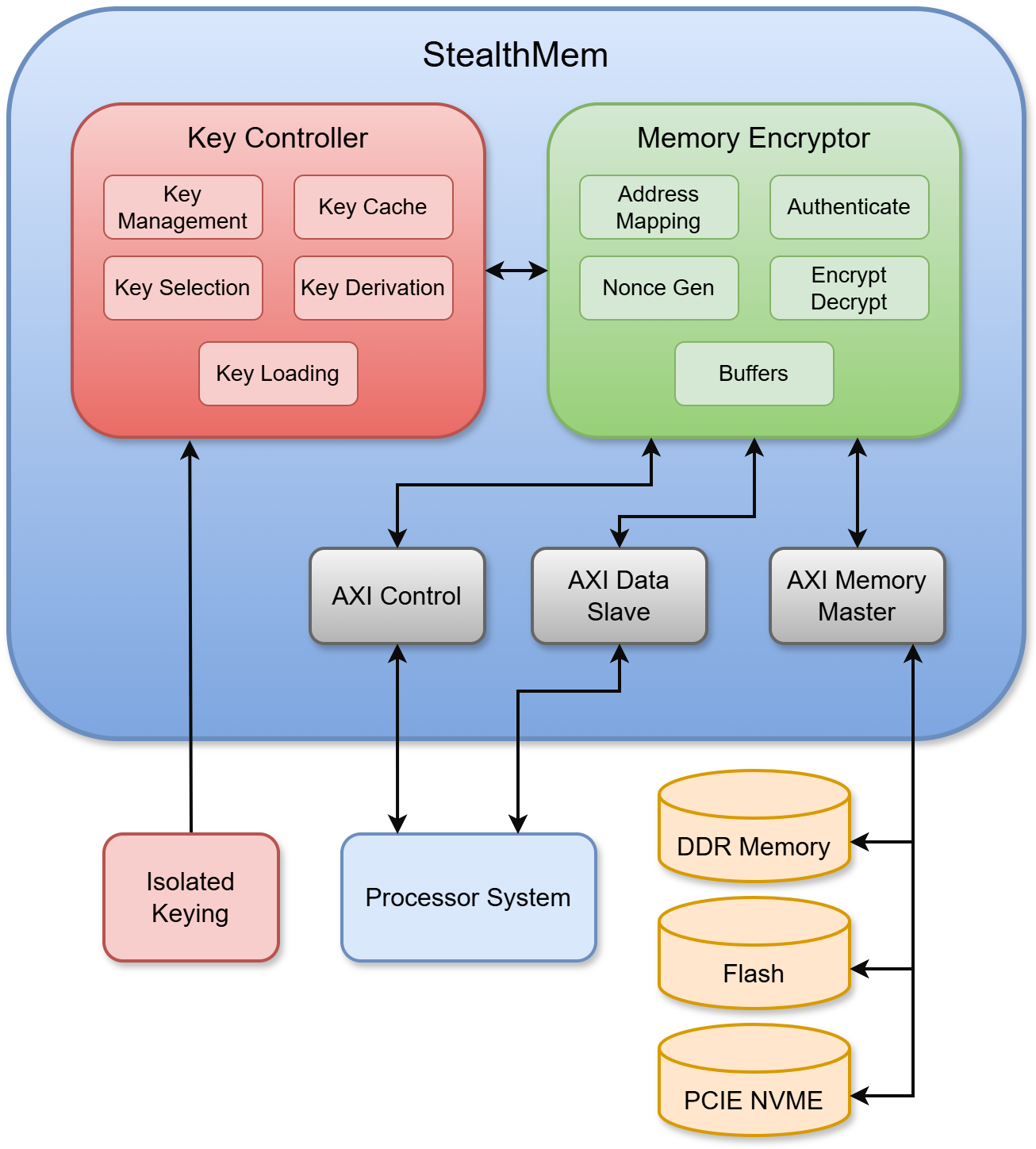
Comprehensive memory encryption with AXI bus mastering and hardware-based key management
Advanced Memory Encryption IP With Comprehensive Security
StealthMem delivers comprehensive security for your entire memory ecosystem through high-performance encryption and authentication. Built on our industry-leading StealthAES technology, StealthMem seamlessly integrates into FPGA and ASIC designs with advanced features including AXI bus mastering, hardware-based key management, and proprietary StealthCores security architecture.

Comprehensive memory encryption with AXI bus mastering and hardware-based key management
StealthMem encrypts and authenticates memory reads and writes in real time, supporting RAM, flash, and NVMe interfaces. Designed to protect software and sensitive data from physical attacks and reverse engineering.
StealthMem leverages the verified countermeasures from StealthAES, tested with over 1 billion operations and validated using both TVLA and template attacks. Secure key storage and non-deterministic data paths ensure your keys and plaintext remain protected.
With full AXI master capabilities, StealthMem interacts directly with system memory, minimizing latency and CPU overhead. Fully compatible with AXI4 and AXI4-Lite interconnects for seamless integration into your existing architecture.
Integrated secure key vault with hardware-enforced access controls enables flexible key rotation, secure storage, and cryptographic isolation across different memory regions and security domains. Keys are securely loaded and decrypted for non-volatile memories, ensuring protection throughout the entire key lifecycle.
StealthMem is available in multiple configurations optimized for area, performance, or power, depending on your memory bandwidth and latency needs.
Combining confidentiality, integrity, and authenticity in a single solution prevents both data exposure and tampering attacks on your critical memory assets.
StealthMem protects against sophisticated physical attacks including probe attacks, bus snooping, and memory extraction attempts. Real-time encryption ensures data remains secure even if physical access is compromised.
Inheriting proven countermeasures from StealthAES, StealthMem provides industry-leading resistance to power analysis, electromagnetic emanation attacks, and timing attacks with over 1 billion trace resistance.
Hardware-based key vault with cryptographic isolation ensures keys are never exposed in plaintext. Support for key rotation, secure loading, and multi-domain key management.
GCM mode provides both encryption and authentication, detecting any tampering attempts and ensuring data integrity throughout the memory lifecycle.
Built on our industry-leading StealthAES technology with verified side-channel countermeasures tested across billions of operations.
AXI-compatible interfaces and comprehensive documentation ensure rapid deployment in existing FPGA and ASIC designs.
Decades of cryptographic implementation experience with dedicated integration support to ensure successful deployment.
Designed for commercial, industrial, and defense applications requiring the highest levels of security and reliability.
For detailed area and performance data, implementation guidelines, and information on different configurations and target devices, contact the StealthCores team today. Let our security experts help you integrate StealthMem into your design with maximum efficiency and protection.